How Many Cyberattacks Per Day: Key Highlights
-
600 million cyberattacks hit Microsoft customers daily.
-
53% of reported 2025 cyberattacks were system intrusions.
-
The global cost of cybercrime could reach $15.63 trillion by 2029.
The systems built to protect your data can become the very paths that let attackers in.
In the second quarter of 2025 alone, 93.64 million user records were breached worldwide, turning data from an asset into a liability in a matter of seconds.
All it takes is one distracted click or overlooked update to give them the opening they’re waiting for.
In this post, we’ll explore how many cyberattacks per day target digital systems worldwide and what those numbers reveal about the unseen battles shaping your company’s future.
How Many Cyberattacks Happen Per Day?
How many data breaches happen every day?
Attackers are executing billions of scans to uncover vulnerabilities, using that intelligence to launch targeted ransomware campaigns and other high-impact intrusions.
The data below highlights how widespread these breaches have become and the growing pressure they place on security teams.
- According to the Microsoft Digital Defense Report, the company’s customers face more than 600 million cyberattacks per day, spanning everything from phishing to ransomware.
- In 2024, Microsoft cyberattack incidents highlighted how aggressively threat actors are targeting technology-driven organizations, with IT leading as the most attacked sector worldwide at 24%.
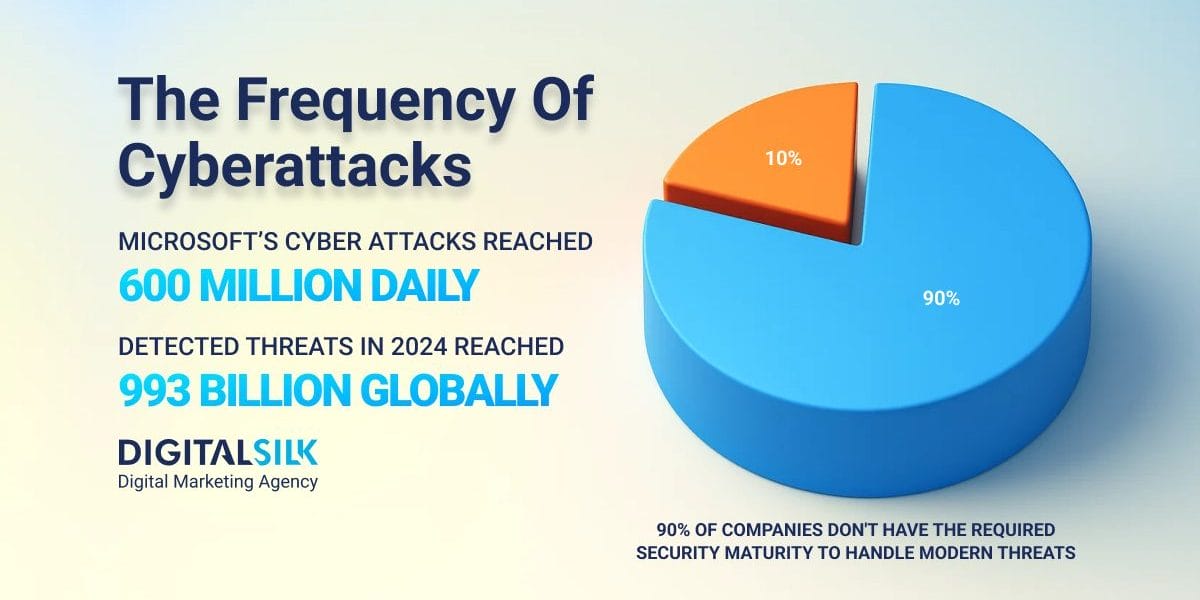
- 90% of organizations have at least one exposed attack path and the waves of cyberattack Microsoft faces show how relentless these threats have become.
- 80% of organizations have attack paths that put their most critical assets at risk.
What These Numbers Mean For You
- Integrate security into emerging web development trends. Building protections into new digital products from the start helps prevent adding new vulnerabilities.
- Eliminate exposed attack paths before expanding systems. Closing known weaknesses now reduces the risk of large-scale breaches as your infrastructure grows.
- Strengthen brand trust with transparency. Publicly showing how your company safeguards data can reduce the reputational damage that follows a breach.
How Many Cyberattacks Per Year Occur Across Digital Systems?
The sheer volume of attacks has turned cybersecurity from a technical concern into a core operational priority.
Cybercriminals are scaling their efforts with automation and reconnaissance, probing for weaknesses across every layer of digital infrastructure.
The data below highlights the growing number of cyberattacks per year and how their reach is reshaping risk for businesses worldwide.
- Based on the Microsoft Digital Defense Report, the daily average of 600 million cyberattacks on its customers reveals a staggering number of cyberattacks per year at about 219 billion worldwide.
- Attackers are now using large-scale reconnaissance techniques to map exposed digital infrastructure and vulnerabilities, driving 993 billion detections in 2024 and revealing how many cyberattacks per day organizations could be facing.
- In 2024, North America accounted for 24% of all enterprise cyberattack incidents worldwide.
- The Federal Bureau of Investigation (FBI) received 859,532 complaints of suspected internet crime in 2024.
- Phishing or spoofing was the most reported crime type, with 193,407 reports.
- The Identity Theft Resource Center received 3,158 reports of data compromises and victim notices in 2024.
What These Numbers Mean For You
- Map your full digital footprint. Large-scale reconnaissance targets overlooked systems, so catalog and assess every connected asset regularly to prevent disruptions that break customer engagement.
- Focus defenses on high-traffic systems. Attackers concentrate efforts where activity is dense, making core platforms and gateways priority targets for protection.
- Build controls for automated attack volume. Daily high-frequency attempts require scalable defenses that keep services stable and user interactions consistent, reinforcing long-term loyalty.
How Often Do Cyberattacks Occur, By Type?
Cyberattacks take many forms, from system intrusions and phishing to ransomware and web application exploits, each exposing different weaknesses.
Understanding how these attack types are distributed helps reveal where defenses are breaking down and which methods are causing the most damage.
The data below shows how tactics, entry points and motivations are shaping the current threat landscape.
- Hacking accounted for 29.1% of cyber incidents in organizations worldwide as of September 2024, making it the most common type reported.
- External and internal threat actors were detected at nearly the same rate in cyber incidents, at 47.61% and 47.35% respectively.
- 53% of cyberattacks reported in 2025 were a system intrusion.
- Financial gain was the primary motive for 89% of cyber incidents, followed by espionage with 17%.
- 60% of 2025 cyberattacks involved a human element, while 30% involved a third-party.
- Web applications were the top entry point, involved in 34% of reported cyber incidents.
- 30% of compromised systems were enterprise-licensed devices, while 46% of those with corporate logins were unmanaged personal devices.
- In 2024, 41% of security officers worldwide cited ransomware as the leading cyber risk expected over the next five years.
- Ransomware attacks impacted 59% of organizations globally in 2024.
- Known or unknown security gaps are the top reason for ransomware attacks, or 65% of total cases.
- 50% of all ransomware attacks in 2025 resulted in encrypted data.
- 97% of organizations were able to recover their encrypted data, either by paying the ransom or using backups.
- The average ransom demand fell by 34%, dropping to $1,324,439 in 2025 from $2 million in 2024.
- In the third quarter of 2024, there were 989,123 phishing attacks worldwide.
- 65% of phishing attacks in 2024 targeted organizational assets, as opposed to personal ones.
What These Numbers Mean For You
- Reduce human-driven risk. Most attacks involve human error or misuse, making regular training and access control essential for safeguarding operations.
- Protect core platforms. Web applications are a top entry point, so secure the systems that directly support lead generation and customer interactions.
- Secure third-party access. External vendors and tools can create hidden vulnerabilities, so monitor their permissions to prevent breaches that weaken brand preference.
How Organizations Are Managing Cyberattacks In 2025
How many cyberattacks per day can organizations realistically defend against?
As daily threats grow in volume and complexity, companies are under pressure to strengthen their security foundations and adapt faster to emerging risks.
The data below explores how organizations are approaching cybersecurity in 2025.
- The annual cost of cybercrime reached $10.29 trillion dollars in 2025.
- By 2029, the increase in cyberattacks on a global level is projected to push those costs to $15.63 trillion.
- The average cost per data breach in the U.S. was $9.36 million in 2024.
- In 2024, the monetary damage in the U.S. caused by cybercrime reached a historical peak of $50.5 billion.
- In 2025, organizations need 181 days to identify a breach and 60 days to contain it, falling to a nine-year low and extending the decline that began after the 2021 peak.
- 65% of businesses are still struggling to fully recover from data breaches.
- 50% of the time, the organization’s security teams and tools are responsible for breach identification, while only 19% of them receive disclosure from the attacker.
- 47% of businesses consider lost customer trust the most significant consequence of cyberattacks.
What These Numbers Mean For You
- Link security investments to ROI. Use the rising cost of cybercrime to justify stronger upfront funding for prevention, showing how it reduces long-term financial losses.
- Shorten breach detection timelines. Invest in faster monitoring and automated alerting to cut down the months-long gap that inflates recovery costs and damages ROI.
- Track recovery effectiveness. Measure how quickly systems return to full capacity after breaches to evaluate the ROI of your incident response strategy.
Why Prevention Beats Recovery: The ROI Of Cybersecurity
For many enterprises, cybersecurity is still seen as a cost center, but the data shows otherwise, as proactive defenses are far cheaper than post-breach recovery.
The average data breach in the United States cost $10.22 million in 2025, while the global number totalled $4.44 million in 2025.
Implementing advanced endpoint detection and response (EDR) platforms, such as Microsoft Defender for Endpoint or CrowdStrike Falcon, typically costs between $60 and $185 per device annually, meaning that even for 1,000 endpoints, the total annual spend would be around $60,000–$185,000.
If you take into account the average cost of a data breach in the U.S., the EDR investment is well under 2% of the total cost, making prevention dramatically more cost-effective than recovery.
Moreover, IBM’s report highlights that organizations that deployed security AI and automation cut breach lifecycle by 80 days and saved an average of $1.9 million per breach in 2025.
What These Numbers Mean For You
- Think globally & locally. The trillion-dollar figure shows the macro-scale damage, but if you ignore prevention, you could face disproportionately large losses.
- Invest early to reduce losses. EDR and automated monitoring cost a fraction of a single breach, yet mitigate millions in potential damages.
- Track ROI with metrics. Measure time-to-detect and cost-per-incident reductions to show how prevention protects revenue and trust.
The Role Of AI In 2025 Cyberattacks
The growing use of AI is reshaping how cyberattacks are both launched and defended against.
Organizations are adopting this technology to enhance detection, accelerate response and anticipate threats, even as new AI-driven risks emerge alongside these tools.
The statistics below shows how AI is transforming cybersecurity strategies, capabilities and workforce demands across the industry.
- The value of the global AI cybersecurity market is expected to reach $133.8 billion by 2030.
- More than 90% of AI-driven cybersecurity capabilities are anticipated to originate from third-party providers.
- 95% of cybersecurity professionals believe AI-powered solutions can greatly boost the speed and efficiency of their defenses.
- 65% of businesses say they view AI-powered threats as separate from non-AI threats.
- Cloud security is seen as the top area where defensive AI will make the biggest difference, according to 66.4% of professionals.
- 43.1% of businesses are using AI technology as part of their cybersecurity strategy.
- 56.9% of businesses that use AI apply it for anomaly detection systems.
- 82% of security operations centers (SOCs) say integrating AI has improved their threat detection capabilities.
- 66.5% of businesses anticipate rising demand for professionals with AI and cybersecurity expertise over the next five years.
- The biggest challenge when implementing AI in cybersecurity is the lack of skills when recruiting new staff or the lack of knowledge of current employees, according to 33% of professionals.
What These Numbers Mean For You
- Measure performance improvements. Track how AI adoption impacts detection rates, response times, and operational costs to refine strategy over time.
- Assess reliance on third-party AI tools. Evaluate vendor security standards and data handling practices before adopting externally developed AI capabilities.
- Balance AI with human oversight. Pair automated tools with skilled analysts to catch context-driven threats AI might miss.
Improve Your Website Security With Digital Silk
The sheer scale of today’s threats makes website security impossible to overlook, with how many cyberattacks per day in the world proving just how constant the pressure has become.
Every breach risks lost revenue, operational downtime and weakened customer trust, so proactive protection must be treated as a core business priority.
Digital Silk uses industry-leading security practices, advanced monitoring and tailored strategies to safeguard your website against evolving threats.
As a professional web development agency, our services include:
- Custom web development
- Website maintenance
- eCommerce development
- Custom web design
- Branding strategies
- Digital marketing
Our experts emphasize proactive management and open communication to ensure every partnership delivers tangible results.
Contact our team, call us at (800) 206-9413 or fill in the Request a Quote form below to schedule a consultation.
"*" indicates required fields