WordPress Hardening: Key Highlights
-
Scale creates constant exposure: With WordPress powering roughly 43% of all websites globally, its scale makes it a continuous target for automated attacks. Security failures are discovered quickly, often within hours, not weeks.
-
Most breaches exploit basics, not sophistication: Web application breaches commonly stem from known vulnerabilities and weak access controls, not advanced exploits.
-
Hardening becomes a resilience strategy: WordPress hardening is a strategic requirement for protecting performance, trust and long-term digital resilience as websites take on greater revenue and brand responsibility.
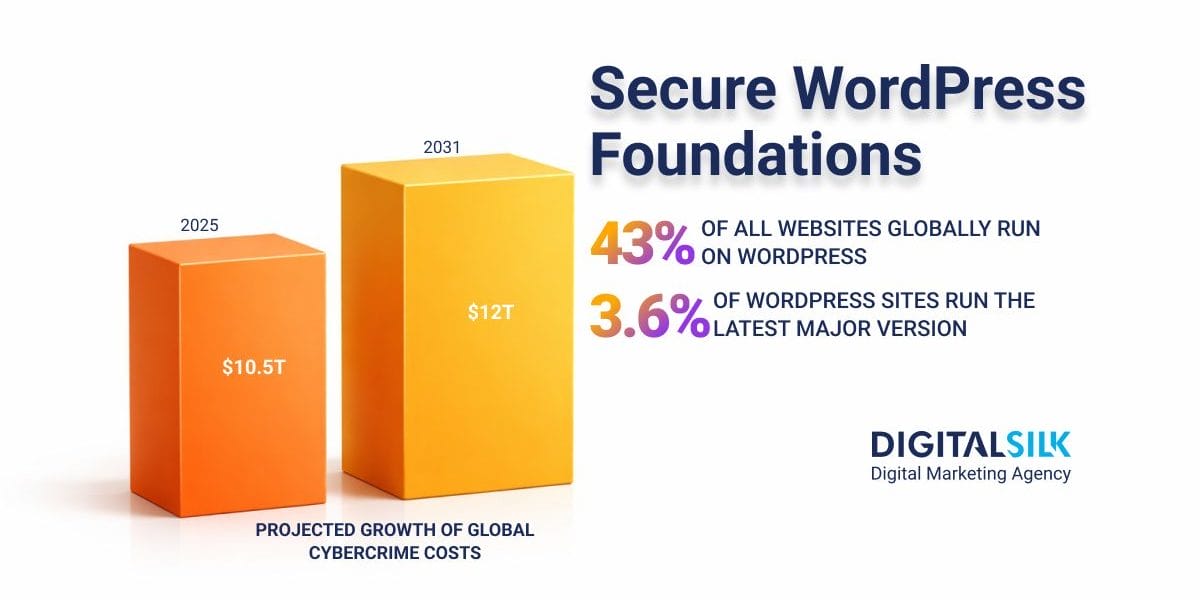
WordPress remains the most widely used content management system in the world, powering approximately 43% of all websites globally in 2025.
That scale also makes it a prime target.
The Verizon 2024 Data Breach Investigations Report, which analyzed 10,626 confirmed breaches across 94 countries, shows that web applications are involved in more than a quarter of all breaches, most often due to known vulnerabilities and weak access controls.
For WordPress sites, this means security failures rarely start with sophisticated attacks.
They begin with missed updates, excessive permissions, unsecured login paths or infrastructure not designed for persistent threat exposure.
In 2026, hardening WordPress is a strategic requirement for protecting performance, trust and long-term digital resilience.
The 2026 WordPress Hardening Model
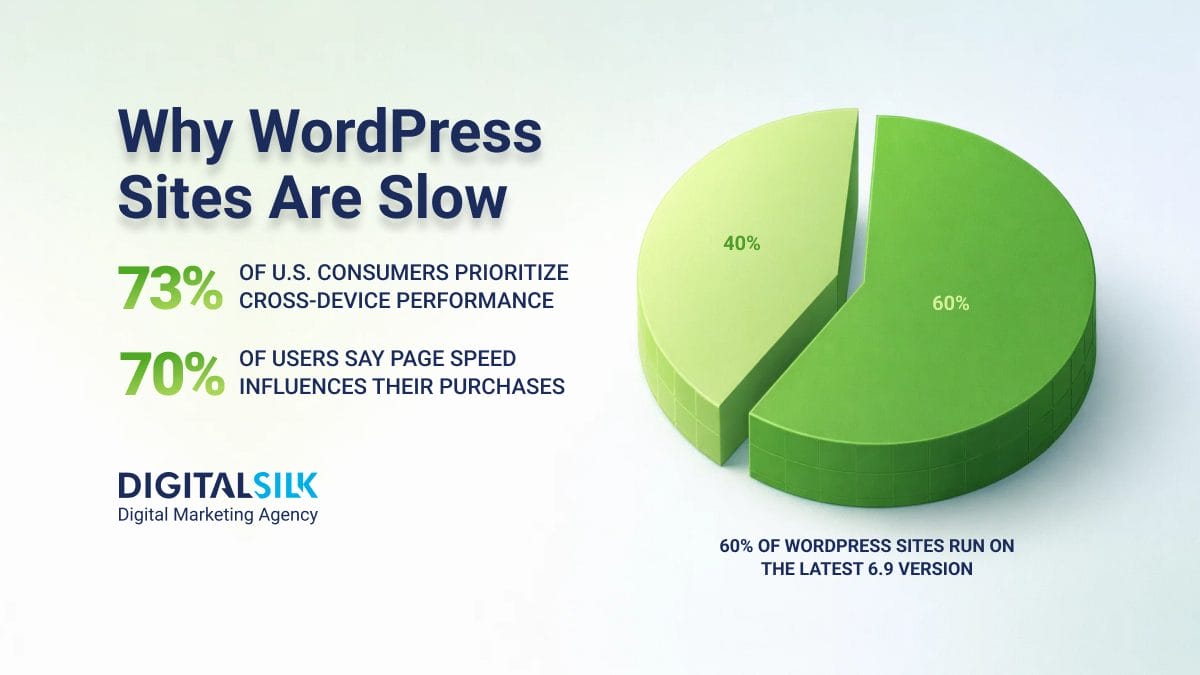
Only about 3.6% of WordPress sites were running the most recent major version in 2025, with the majority still on prior releases.
While this doesn’t capture every security patch cadence, it illustrates that most sites lag behind the latest version, leaving them more exposed to vulnerabilities that are mitigated in newer releases.
Your website’s security is vital for protecting business data, but it’s also essential for building trust and credibility with your visitors.
This is one of the first questions businesses ask when evaluating WordPress: Is the site kept up to date and secure? Lagging versions are a real risk because they often lack recent security improvements and can be easier for threat actors to exploit if known vulnerabilities remain unpatched.
Instead of a flat list, this guide follows how real attacks unfold:
- Tier 1. Stop the most common break-ins: Fast, high-impact controls that block the majority of real-world compromises.
- Tier 2. Limit damage when something goes wrong: Configuration and platform decisions that contain risk instead of letting it spread.
- Tier 3. Detect, respond and recover: Controls that don’t prevent incidents, but make them survivable.
Tier 1: The Fastest Risk Reduction
These controls focus on the attack paths that are hit first and most often.
WordPress sites are not breached because attackers spend weeks crafting bespoke exploits. They are breached because automated tools scan at massive scale, looking for predictable weaknesses.
A recent Forbes report illustrates just how aggressive this background activity is.
Across just 48 hours in October 2025, 1.6 million attack attempts were recorded against WordPress-powered sites.
These were largely automated probes targeting exposed login pages, weak credentials and misconfigured admin access. At this scale, even small security gaps are discovered quickly, which is why reducing exposure at the identity and login layer delivers the fastest risk reduction.
1. Use Strong Passwords
Did you know that commonly used passwords such as “123456“ and “password” are still prevalent among internet users?
Passwords are still the weakest link in most WordPress breaches.
This doesn’t just mean your WordPress admin login. It includes:
- Hosting control panels
- FTP/SFTP credentials
- Database users
- Email accounts tied to password resets
One of the simplest things you can do to improve security on your website is to use unique, complex passwords for all user accounts, including your WordPress admin account.
Strong passwords should be:
- Generated by a password manager
- At least 12 characters
- Unique for every system
If one password is reused across services, a breach elsewhere can become a WordPress breach without touching your site directly.
2. Enable Two-Factor Authentication
Two-factor authentication adds a second barrier that stolen passwords can’t bypass on their own.
This is one of the highest-impact security improvements you can make, especially for:
- Administrators
- Editors
- Anyone with plugin or theme access
If a single admin account is compromised without MFA, the entire site is effectively compromised.
3. Eliminate Shared Admin Accounts
Shared logins make accountability impossible and breaches harder to trace.
Every person who accesses the site should have:
- Their own account
- The lowest permission level required
- Access removed immediately when it’s no longer needed
If “everyone is an admin,” one mistake becomes everyone’s problem.
4. Limit Login Attempts & Add Rate Limiting
Limiting login attempts can prevent brute force attacks, where hackers try to guess your password by repeatedly attempting to log in.pl
Brute-force login attempts are constant background noise on WordPress sites.
Limiting login attempts and adding rate limiting prevents attackers from guessing passwords indefinitely and reduces server load caused by automated traffic.
This should be handled either:
- Through a security plugin, or
- At the hosting / firewall level
5. Secure The wp-admin & wp-login.php Endpoints
The WordPress admin area is the most valuable target on your site.
At a minimum:
- Force HTTPS
- Protect against automated bot traffic
- Add monitoring for repeated failed attempts
For higher-risk sites, restricting access by IP or location can dramatically reduce exposure.
6. Change The Default Login URL (With Context)
Changing /wp-admin or /wp-login.php alone is not a security solution.
Automated tools are designed to discover login endpoints, regardless of the URL.
Where this step becomes useful is when it’s paired with core access controls.
When combined with:
- Rate limiting or brute-force protection, which caps repeated login attempts
- Bot filtering or a web application firewall, which blocks known automated traffic before it reaches WordPress
- Two-factor authentication for admin users, which prevents access even if credentials are exposed
Changing the login URL can meaningfully reduce automated noise and opportunistic attacks.
This is especially important when you know that automated pressure is increasing, not decreasing.
According to Google Cloud’s Cybersecurity Forecast 2025, attackers are increasingly using AI and automation to scale credential abuse, phishing and web-level exploitation.
These systems can rotate IPs, adapt request patterns and probe defenses continuously, making unprotected login endpoints an easy target.
Rate limiting, bot filtering and layered authentication controls are necessary responses to an environment where attacks are automated by default.
7. Disable Username Enumeration
By default, WordPress can expose usernames through predictable URL patterns and endpoints.
Blocking username enumeration prevents attackers from easily discovering valid usernames before attempting password attacks.
This removes a key input attackers rely on and makes brute-force and credential-stuffing attempts less effective.
It’s a small change that quietly removes unnecessary visibility.
8. Disable XML-RPC If You Don’t Need It
XML-RPC is frequently abused for brute-force amplification and automated credential attacks.
If your site does not rely on XML-RPC for integrations or publishing workflows, disabling it removes a common attack vector with little downside.
Many sites leave it enabled by default without realizing it’s not being used.
If XML-RPC is required, it should be tightly restricted and monitored.
9. Keep WordPress Core, Plugins & Themes Updated
Most known WordPress vulnerabilities are patched quickly but only if updates are applied.
Delaying updates creates a predictable window where automated tools can exploit publicly known issues at scale.
This is especially true for plugins, which are the most common source of new vulnerabilities.
Updates should be:
- Tested in staging when possible
- Applied consistently
- Owned by a clearly defined role, not “whenever someone remembers”
Patch discipline is one of the strongest defenses available.
10. Remove Unused Plugins & Themes Completely
Deactivated plugins and themes still exist on your server and can still contain vulnerabilities.
Removing unused components reduces your attack surface, simplifies maintenance and makes it easier to keep everything else updated.
Fewer moving parts mean fewer places for problems to hide.
If a plugin no longer serves a clear purpose, it doesn’t belong on the site.
11. Be Selective About New Plugins
Every new plugin adds code, complexity and potential risk.
Before installing anything new, it’s worth checking update history, confirming active maintenance and avoiding overlapping functionality.
Well-supported plugins with a clear purpose are always preferable to stacking multiple tools that do similar things.
Security often improves more by removing plugins than by adding them.
Tier 2: Platform & Configuration Hardening
Tier 2 controls are designed to contain risk, reduce blast radius and prevent a single failure from escalating into a broader incident.
12. Use Secure Hosting & Isolate Environments
WordPress security starts below WordPress itself, at the hosting and infrastructure level.
A hardened setup separates production from staging or development environments, restricts who can deploy changes and limits server-level permissions.
This prevents testing mistakes or compromised credentials in one environment from affecting the live site.
Hosting decisions directly influence how far a breach can spread.
13. Add A Web Application Firewall (WAF)
A web application firewall filters malicious traffic before it reaches WordPress.
It helps block known exploit patterns, credential-stuffing attempts and automated scanning at the network edge.
This reduces server load and prevents many common attacks without requiring WordPress itself to handle them.
A WAF is not a replacement for hardening, but it significantly reduces background threat noise.
14. Lock Down File Permissions
File permissions control who can read, write or execute files on your server.
Overly permissive permissions make it easier for attackers to modify files or run malicious scripts.
Restricting permissions to the minimum required limits what can be changed, even if access is gained.
Permissions should be reviewed periodically, especially after migrations or hosting changes.
15. Disable File Editing In The WordPress Admin
By default, WordPress allows administrators to edit plugin and theme files directly from the dashboard.
Disabling file editing removes a common shortcut that attackers use after gaining admin access.
It also prevents risky live edits on production sites.
File changes should happen through controlled deployment workflows, not the admin interface.
16. Prevent PHP Execution In Uploads
The uploads directory is one of the most common targets in WordPress attacks.
If an attacker can upload a file and execute PHP from that directory, they can gain persistent control without full admin access.
Blocking PHP execution in uploads prevents this escalation path.
This is a containment control that quietly stops many real-world compromises from going further.
17. Disable Directory Browsing
Directory browsing allows visitors to see file and folder listings when no index file is present.
This exposes site structure and sometimes sensitive assets that were never meant to be public.
Disabling directory browsing removes unnecessary visibility and limits reconnaissance opportunities for attackers.
It’s a simple change with no downside for legitimate users.
Tier 3: Monitoring, Recovery & Resilience
Even well-hardened systems can be compromised. What separates resilient organizations from vulnerable ones is how quickly they detect issues and recover.
Global cybercrime damages are projected to reach approximately $12 trillion by 2031.
That figure includes not just breaches, but downtime, recovery costs, lost revenue and long-term reputational damage. Monitoring, logging and recovery controls are what limit the financial and operational impact when prevention alone is not enough.
However, when prevention and containment are not enough, Tier 3 controls determine how quickly an organization can regain stability.
18. Log User Activity
User activity logs record important actions such as logins, permission changes and plugin updates.
These logs help you understand what changed, when it changed and who initiated it.
Without logging, investigating incidents becomes guesswork and recovery takes longer.
Visibility is essential once something goes wrong.
19. Monitor What Actually Matters
Effective monitoring focuses on signals that indicate real risk.
This includes:
- Login activity
- File changes
- Plugin or theme modifications
- Privilege escalation
Too many alerts lead to alert fatigue, which causes real issues to be missed.
Fewer, meaningful alerts are far more valuable than constant notifications.
20. Back Up Your Site & Test Restores
Backups are the last line of defense when everything else fails.
A reliable backup strategy includes automated backups, off-site storage, versioning and periodic restore tests.
If you’ve never tested a restore, assume it won’t work when you need it.
Backups are boring until they’re the only thing standing between you and a rebuild.
21. Secure wp-config.php & Sensitive Files
Configuration files such as wp-config.php contain credentials and security-critical settings.
Restricting access to these files prevents attackers from extracting secrets or altering core configuration. These files should never be publicly accessible.
Protecting them limits how much damage a partial compromise can cause.
22. Limit Database User Privileges
The WordPress database user should only have the permissions required to function.
Excessive database privileges allow attackers to read, modify or delete more data than necessary if access is gained.
Limiting permissions helps contain the impact of a breach.
This is an often-overlooked but important containment measure.
23. Use HTTPS Everywhere
HTTPS encrypts data exchanged between your site and its visitors.
This protects login credentials, form submissions and session cookies from interception.
Modern browsers and search engines expect HTTPS as a baseline requirement.
Without it, user trust and search visibility can suffer.
24. Prepare An Incident Response Plan
Even well-hardened sites can be compromised.
An incident response plan defines who responds, what gets checked first, how access is revoked and how restoration happens.
Planning ahead reduces downtime, confusion and compounding mistakes during stressful situations.
Calm, prepared responses limit long-term damage.
25. Review Security Quarterly
Security doesn’t stay intact on its own.
Over time, users accumulate access, plugins get added and configurations drift.
A quarterly review helps catch small issues before they turn into real problems.
Consistency is what keeps hardening effective long term.
Why Harden Your WordPress Website?
WordPress hardening is no longer a purely technical exercise.
As websites take on a larger role in revenue generation, lead acquisition and brand credibility, their security posture increasingly becomes a business concern.
McKinsey & Company’s 2025 technology outlook highlights that cybersecurity and digital risk are now viewed as strategic priorities by enterprise leadership, not just operational responsibilities for IT teams.
Website compromises today can disrupt marketing pipelines, expose customer data and damage trust long before infrastructure-level systems are affected.
1. Protect Your Website From Security Threats
Websites are regularly targeted by hackers and malware, and without proper security measures in place, your website can become vulnerable to attacks.
By implementing security measures such as firewalls, anti-virus software and strong passwords, you can safeguard your website from security threats and prevent unauthorized access.
These security measures can also help you detect and respond to security breaches quickly and efficiently, minimizing potential damage.
2. Ensure Data Privacy
If your website collects sensitive user data, such as login credentials or payment information, hardening your WordPress site is crucial to ensuring that this data remains secure and private.
Data breaches can cause significant harm to your business, customers and brand reputation, leading to loss of trust and credibility.
By implementing security measures such as encryption, access controls and secure hosting, you can protect user data from unauthorized access and theft.
Ensuring data privacy can also help you comply with data protection regulations such as GDPR and CCPA, so you can avoid legal penalties and reputational damage.
3. Boost Website Performance
Implementing security measures can also improve the performance of your website. Resource-intensive attacks, such as Distributed Denial of Service (DDoS) attacks, can slow down your website and cause it to crash.
By preventing these attacks through security measures, such as Content Delivery Networks (CDNs) and caching, you can ensure that your website runs smoothly and provides a positive user experience.
Additionally, a secure website can improve your search engine ranking, as search engines prioritize secure websites in their search results. This can lead to increased traffic and improved business outcomes.
The 2026 WordPress Hardening Checklist
WordPress hardening works best when it follows a simple rhythm: stabilize first, then maintain consistently.
The goal is to reduce risk quickly, close the most obvious gaps and then keep things from quietly drifting back into a vulnerable state over time.
Initial Hardening Sprint
This first pass focuses on the entry points attackers use most often. I
t’s not exhaustive, but it delivers the biggest risk reduction in the shortest amount of time.
Most sites can complete this sprint quickly and the payoff is immediate.
- Enforce strong authentication and least-privilege access: Administrative access should be limited to people who genuinely need it. Eliminate shared admin accounts, require two-factor authentication for privileged users and assign roles based on responsibility rather than convenience. Identity is one of the most common failure points in WordPress security, so tightening access early pays off fast.
- Update everything and remove what you don’t need: Apply updates to WordPress core, plugins and themes and permanently remove anything that’s no longer in use. Deactivated plugins still exist on the server and still expand the attack surface. Fewer components mean fewer vulnerabilities to track and fewer surprises later.
- Secure login paths and admin access: Reduce exposure around login and administrative endpoints. Limit brute-force attempts, block obvious bot traffic and make sure admin access isn’t unnecessarily exposed to the public internet. These steps don’t stop every attack, but they dramatically cut down on automated probing and background noise.
- Apply configuration and file hardening: Lock down file permissions, protect sensitive configuration files and disable file editing through the WordPress admin. These controls don’t prevent access on their own, but they limit how much damage can be done if access is gained.
This initial sprint establishes a hardened baseline, one that assumes your site will be scanned, tested and poked at regularly, because it will be.
Ongoing Maintenance
Security doesn’t fail all at once.
It erodes slowly when updates are delayed, access accumulates and nobody is quite sure who still needs permissions.
Ongoing maintenance keeps hardening effective as your site evolves.
- Review updates on a consistent cadence: Establish a predictable update schedule so security patches are applied promptly and safely. Updates should be tested before deployment when possible, but they shouldn’t sit indefinitely. Known vulnerabilities are easiest to exploit when they’re ignored.
- Audit users and permissions quarterly: Periodically review who has access, what level of access they have, and whether it’s still necessary. Remove old accounts, tighten permissions and clean up anything that no longer reflects how the site is actually used.
- Test backups and recovery processes: Backups should be verified through restore testing, not assumed to work. Regular testing ensures recovery is possible under real-world conditions, when time pressure and stress are high.
- Review logs and alerts regularly: Monitoring only adds value when someone looks at it. Reviewing logs and alerts helps surface suspicious behavior early and refine which signals actually matter, instead of reacting to noise.
This cadence turns hardening from a one-time task into a sustainable operating habit.
| PHASE | FOCUS AREA | WHAT TO DO | WHY IT MATTERS |
| Initial Hardening Sprint | Authentication & Access Control | Enforce strong passwords, require MFA for admins, remove shared accounts, apply least-privilege roles. | Blocks the most common account-based attacks. |
| Software & Plugin Hygiene | Update core, plugins and themes. Remove unused components. | Closes known vulnerabilities quickly. | |
| Login & Admin Exposure | Limit login attempts, block bots, restrict admin access where possible. | Reduces automated probing and attack noise. | |
| Configuration & File Hardening | Lock file permissions, protect config files, disable admin file editing. | Limits damage if access is gained. | |
| Ongoing Maintenance | Update Discipline | Apply updates on a consistent schedule with basic testing. | Prevents exposure from delayed patches. |
| User & Permission Reviews | Audit users quarterly and remove stale access. | Prevents permission creep over time. | |
| Backup & Recovery | Test backups through real restore scenarios. | Ensures recovery actually works. | |
| Monitoring & Visibility | Review logs and alerts regularly. | Enables early detection of issues. |
Build A More Resilient WordPress Foundation With Digital Silk
WordPress sites that perform well in 2026 are built on secure, disciplined foundations.
Hardening is now a core part of protecting revenue, customer trust and long-term performance.
That requires a structured approach to access control, platform configuration, monitoring and ongoing risk management.
Digital Silk helps mid-to-large organizations harden and maintain WordPress environments designed to stay secure as sites evolve, scale and attract more attention.
We combine strategy, engineering and ongoing operational discipline to reduce exposure, prevent escalation and keep WordPress sites stable over time.
As an award-winning digital agency, Digital Silk’s services include:
- Custom website design
- Custom website development
- Brand strategy and visual identity
- Rebranding services
- SEO and digital marketing
- UX optimization and conversion-focused design
- Enterprise platforms and integrations
Contact our team, call us at (800) 206-9413 or fill in the Request a Quote form below to schedule a consultation.
"*" indicates required fields